VPN Setup and Config
Project Overview
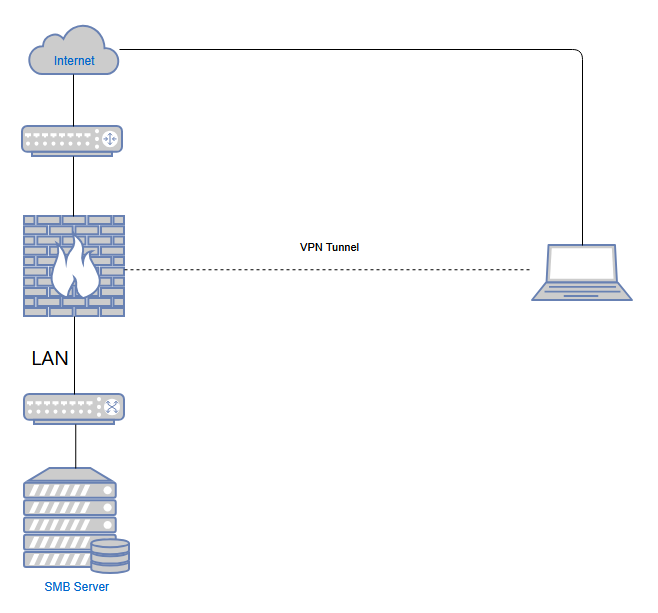
This project involved designing and implementing a secure Remote Access VPN solution on a Cisco ASA 5506-X firewall to enable users on an external network to access internal (Business) resources.
Loading config...
Objectives
- Enable AnyConnect SSL VPN access for remote users.
- Provide secure IP address assignment to VPN clients.
- Configure split tunneling to allow access only to internal resources while leaving Internet traffic local.
- Ensure VPN traffic bypasses NAT and routes correctly to the LAN.
- Integrate VPN behind an ISP router with port forwarding to the ASA.
Network Topology
- External Network → ISP Router (port forwarding enabled).
- Firewall (ASA 5506-X) → Provides VPN services, sits behind router, receives DHCP on outside interface.
- Internal Network (LAN) → protected behind the firewall, contains SMB File Share.
- Internal Admin Network (VPN) → clients receive dhcp addresses the Admin pool.
- Internal General Network (VPN) → clients receive dhcp addresses the General pool.
- Remote users connect via AnyConnect client to the router’s public IP on a specific port.
Images
Implementation Steps
- Create VPN address pools for Admin / General users.
- Define split-tunnel ACLs to specify which internal networks are reachable.
- Create group policies and apply the split-tunnel ACLs.
- Create a tunnel group and link it to the address pool and group policy.
- Configure NAT exemptions so VPN traffic can reach the LAN without being translated.
- On the upstream router, configure port forwarding from the public IP to the firewall’s outside interface.
Testing & Validation
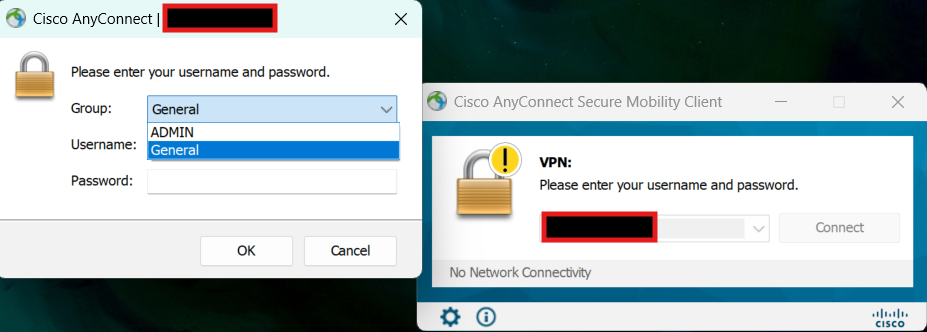
- Connected from an external client.
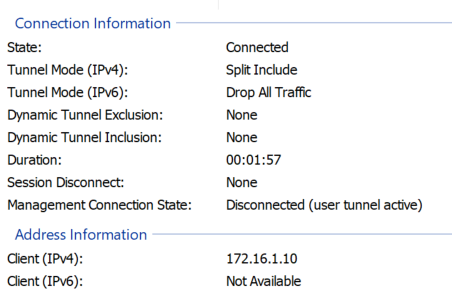
- Confirmed VPN client received an IP.
- Confirmed access to internal LAN resources.
- Verified split tunnel.
Images
Security Improvements
- Use Certificates for Authentication: Deploy certificate-based auth (or combine with MFA) instead of password-only.
- Integrate with External Authentication: Connect ASA to centralized identity (e.g., AD/LDAP/RADIUS) for user management.
- Replace Self-Signed Cert: Install a trusted SSL certificate for the VPN FQDN.
Network Security & VPN Configuration Projects / Professional Experience
- SSL VPN Implementation: Designed and deployed secure SSL VPN solutions for remote access, including client-based and clientless access, integrated with Active Directory, and enforcing split/full-tunneling policies.
- Site-to-Site VPN: Configured IPsec and PPPoE site-to-site VPNs between branch offices and headquarters, ensuring secure communication over Internet and broadband links, with redundancy for high availability.
- Access Control Lists (ACLs) & Segmentation: Implemented ACLs on routers and firewalls to restrict traffic between VLANs, enforce least-privilege access, and protect critical resources.
- Group Policies & User Access Management: Configured AD Group Policies to enforce security settings, role-based access, password policies, and device compliance.
- Additional Security Measures: Deployed NAT, firewall rules, and port forwarding for controlled access; monitored traffic and VPN logs with SIEM tools; conducted vulnerability assessments and applied remediation strategies.