SMB File Share via Windows In-Built Tools
Goal
Create a network shared location to access files as required, as well as host a database file for a later project (Uptime-Kuma, network monitoring).
Networking
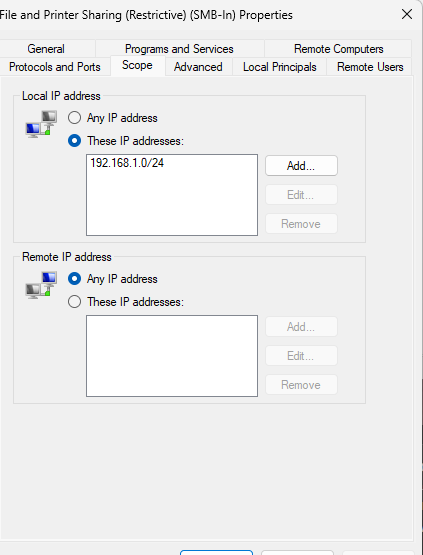
- Configured Windows Firewall to allow access only from specific users within a defined IP address range. Access requires local Windows accounts with passwords.
- In a larger deployment, tighter segmentation could be applied using VLANs, ACLs, or static IP assignments. In this lab setup with only two computers, segmentation was not required.
- The shared folder was created in Windows Computer Management, allowing other computers to connect using DNS (hostname resolution).
- Disabled all “Allow Everyone” network rules to prevent unknown devices from discovering or accessing the share.
Images
Security
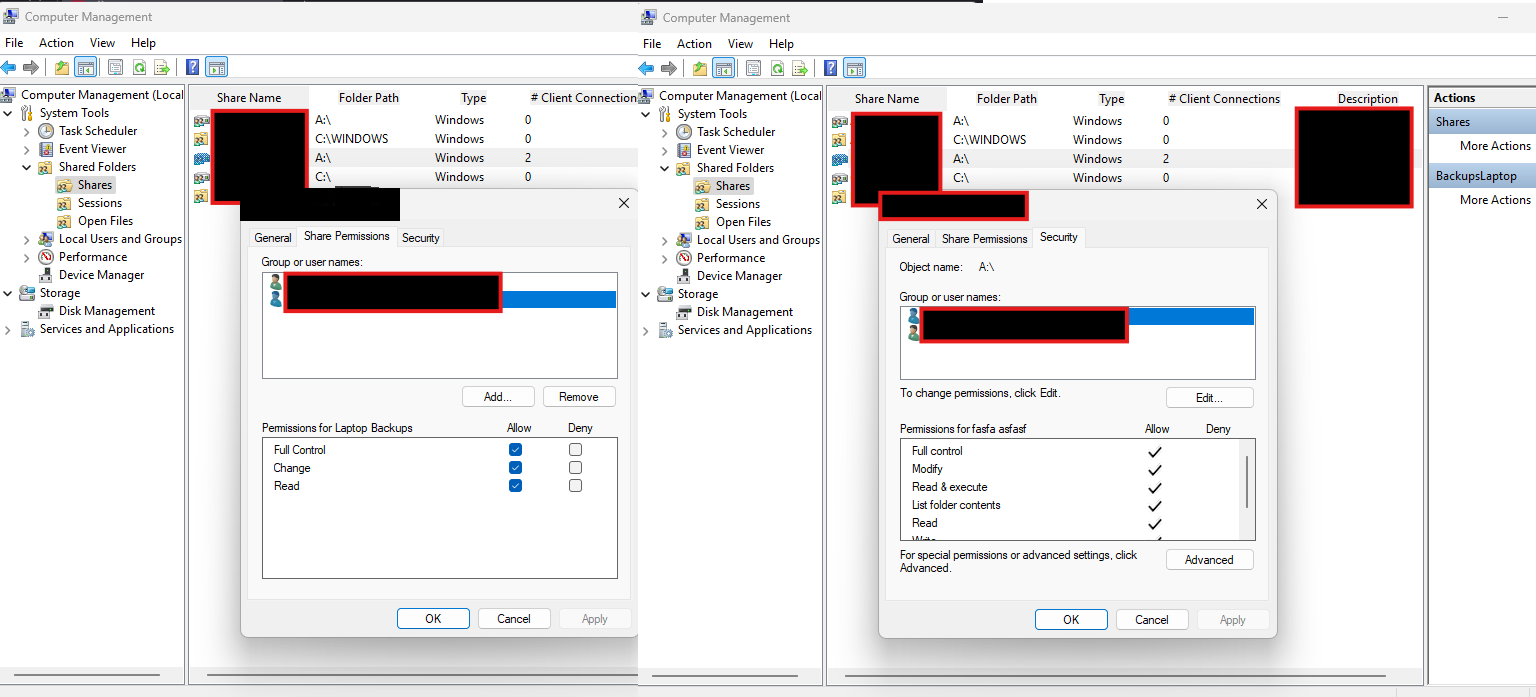
- Configured folder permissions so only specific user groups can read the files. Write access was not required.
- Ensured NTFS permissions and share permissions match, avoiding accidental over-provisioning of access.
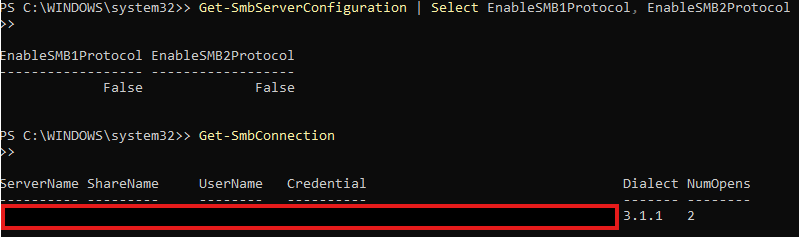
- Disabled legacy and unsafe SMB version (SMBv1) to reduce exposure to known exploits.
- Enabled only SMBv2/3 over TCP port 445, which is supported by all endpoints in the environment.
Images
Testing
- ✅ A computer on the allowed IP range, using an authorized Windows account, successfully connected to the share.
- ❌ A computer outside the allowed IP range, or using an unauthorized account, could not connect.
Images

Outcome
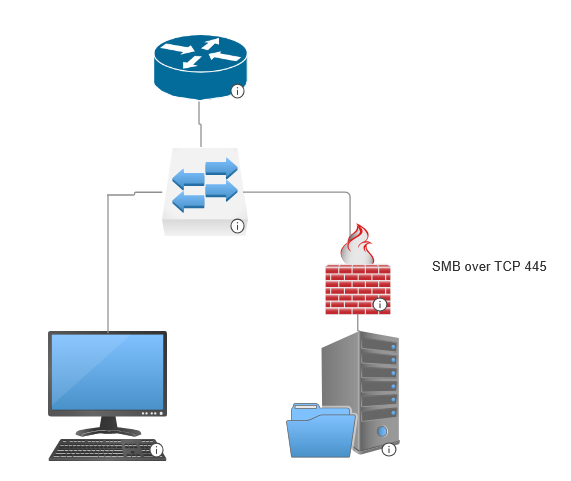
Only trusted, authenticated devices inside the LAN subnet can access the SMB share. Unauthorized devices cannot discover the share via NetBIOS/DNS, and firewall rules block inbound SMB traffic on TCP 445 from outside the allowed range. The setup enforces least-privilege access, uses modern and secure SMB protocols, and reduces the attack surface while meeting the project’s requirements.
Images
Professional Experience
In my IT roles, I work daily with SMB file shares in a production environment. My responsibilities include:
- Creating and managing new file shares for departments and projects, following organizational policies for access control and security.
- Integrating SMB shares with Active Directory (AD), applying group-based permissions to ensure only authorized users and teams can access resources.
- Updating and maintaining shared content, ensuring users have reliable access while adhering to compliance and data retention standards.
- Troubleshooting access issues, often related to group memberships, NTFS/share permission mismatches, or network connectivity.
- Applying security best practices, such as enforcing SMBv3, disabling legacy protocols, and ensuring firewall rules and access controls align with company policies.
I get hands-on experience with this as part of my day-to-day work, so the concepts I’ve shown in my lab project are the same ones I deal with in real-world setups, just at a larger scale with more users and policies involved.